Starting soon: Threat Intelligence Platforms research
In my last threat intelligence blog I discussed my new research on threat intelligence providers. I included a graphic which carved four functional threat intelligence areas: 1) Providers 2) Platforms 3) Enrichment 4) Integration. In December, I will start the next piece of research in the series focusing on Threat Intelligence Platforms (TIPs). This will likely be two reports one focusing on people, process and use cases and the other focusing on the vendor landscape. My presentation at the 2016 SANS Cyber Threat Intelligence Summit will include some perspective on the state of threat intelligence platforms.
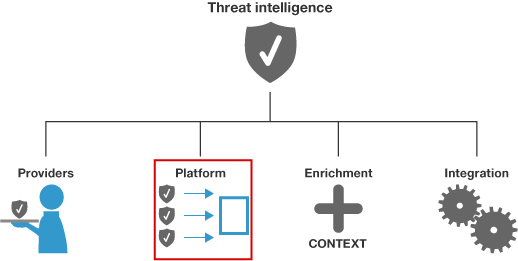
I will be looking into the following functional areas. I'm also going to look beyond TIPs to see how traditional analytics platforms like SIEMs are including these capabilities. I also will look into how SIEMs and TIPs should function in the same environment. I will also address the "roll your own platform" phenomenon that is common in technology firms and large financial institutions. Depending on the size and maturity an organization, multiple solutions could be involved in addressing the use cases, I will also break that functionality out.
- Ingestion
- Enrichment
- Analysis (Important: How does TIP improve tradecraft?)
- Exploration
- Integration
- Collaboration
- Sharing
I touched on TIPs during my RSA Conference talk entitled: "Threat Intelligence is like 3 day potty training." I made the analogy that you must have a quarterback (just not Tony Romo, he gets hurt too often) to orchestrate your threat intelligence activities. Would you rather operationalize like this:
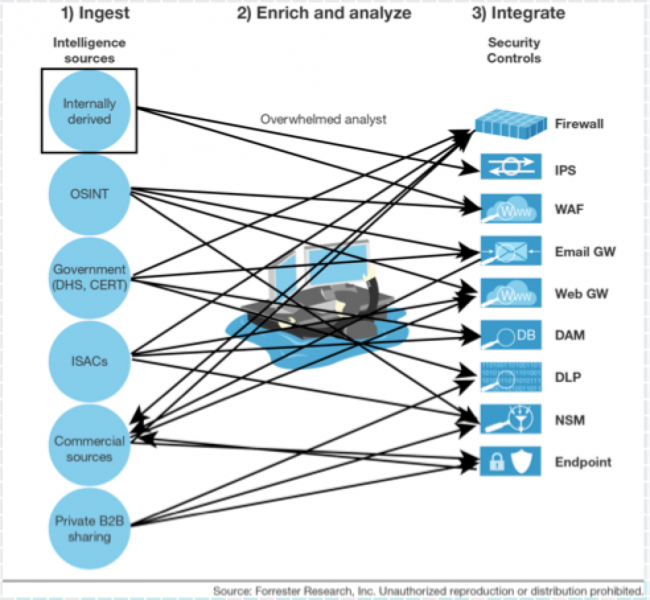
Or like this:
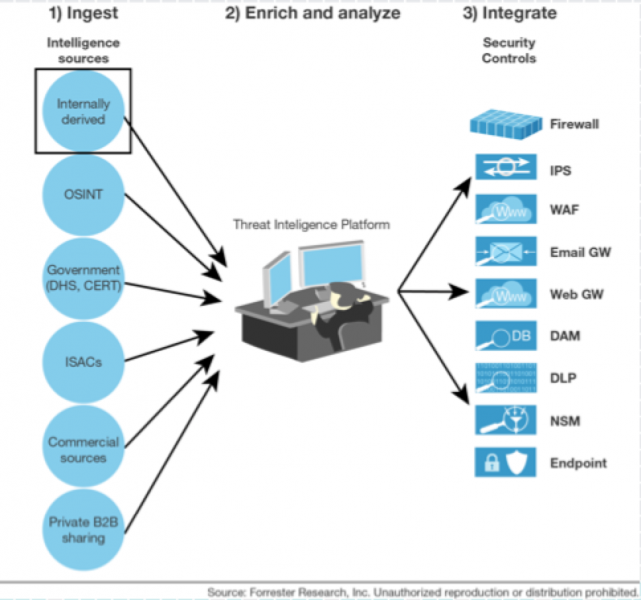 ]
]
The hit list for this research will include vendors like: Brightpoint, EclecticIQ, IBM I2, IID, Maltego, Palantir, SoltraEdge, Splunk, ThreatQuotient, ThreatConnect, and ThreatStream. We will also have our typical batch of enterprise conversations as well.