Maximizing Your Investment In Cyberthreat Intelligence Providers
I just published my latest research on threat intelligence: Vendor Landscape: S&R Pros Turn To Cyberthreat Intelligence Providers For Help. This report builds upon The State Of The Cyberthreat Intelligence Market research from June. In the new research, I divide the threat intelligence space into four functional areas: 1) Providers 2) Platforms 3) Enrichment 4) Integration. This research is designed to help readers navigate the crowded threat intelligence provider landscape and maximize limited investment resources. In this report, we looked at 20 vendors providing a range of tactical, operational, and strategic threat intelligence.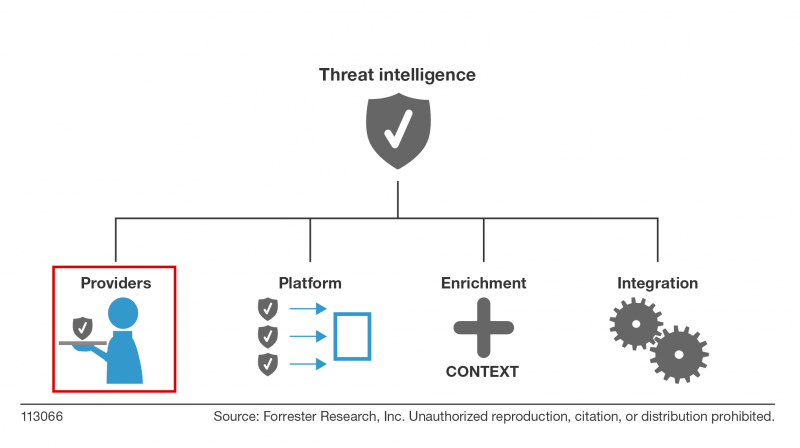
When developing threat intelligence capabilities, one of the most important requirements is to collect and develop your own internal intelligence. Nothing will be as relevant to you as intelligence gathered from your own environment, your own intrusions. Before you invest six figures (or more) in 3rd party threat intelligence, make sure you are investing in your internal capabilities. Relevancy is one of the most important characteristics of actionable intelligence; check out "Actionable Intelligence, Meet Terry Tate, Office Linebacker" for more details on the traits of actionable intelligence.
In the report, I use the traditional intelligence cycle as a framework to evaluate threat intelligence providers. The intelligence cycle consists of five phases:
- Planning and direction. This is the beginning and end of the intelligence cycle. It starts with intelligence requirements that align with business requirements and ends with intelligence products. The successes and failures of previous efforts are reviewed and incorporated into future efforts.
- Collection. In this stage, information is collected based on the businesses' intelligence collection requirements. Internal and external collection is critical. We will discuss types and sources of intelligence in greater detail later in the report.
- Processing. In this stage, technology is leveraged to process raw information into a form that analysts can use. Automated parsing and data deduplication occur in this phase and make the analyst's job much easier.
- Analysis and production. This is one of the most critical stages of the intelligence cycle. Analysts convert information to actionable intelligence and noise becomes signal. Operational and strategic intelligence products are created for stakeholders.
- Dissemination. In the final stage, intelligence products are delivered to consumers. Timely dissemination to requestors is key; actionable intelligence must be delivered in a time frame that supports decision-making. The intelligence cycle begins once again.
The traditional intelligence cycle does have its flaws, the hierarchical model doesn't reflect the real world intelligence operations and intelligence takes to long to be created. As a result, other methodologies have emerged including target centric intelligence and most recently activity based intelligence. Pragmatically speaking, for most commercial organizations the traditional intelligence cycle is more than sufficient to meet your needs. Here is a sampling of suggestions I suggest for evaluating threat intelligence providers:
- Ignore vendors who try to distract you with the size of their threat intelligence (Collection). When it comes to collection, size isn't the most critical input. Don't be distracted by vendors who claim to have the "largest global threat intelligence network on the planet." Claims of "5 million endpoints" or "hundreds of thousands of networks sensors" should go in one ear and out the other. If a vendor's collection capabilities don't produce threat intelligence that is relevant to your organization and threat model, then it's nothing more than window dressing. When it comes to actionable intelligence, relevancy matters.
- Insist on more transparency into sources and methods. Be wary of providers that won't provide any details on their collection capabilities (Collection). One hundred percent transparency isn't realistic; providers naturally want to protect their sources and methods, but they must find a compromise that informs prospects and demonstrates differentiation. In a crowded market, providers who keep everything about sources and methods private will be hard-pressed to make customer shortlists where they will be given the opportunity to validate their nebulous claims. Challenge vendors that provide little detail and suggest nondisclosure agreements; as a last resort, eliminate them from consideration.
- Understand how the providers derive their intelligence (Analysis.) Make sure you understand the analytical process used by the CTI provider to develop intelligence. This is where you find out how the vendor leverages the processing and analysis stages of the intelligence cycle. Some providers are more focused on rules-based engines or predictive analytics while others add an additional layer of human analysis capabilities. Clarify the ratio of technical-to-human analysis, and keep in mind that the more human analysis, the more expensive the CTI offering. For human analysis, does the provider have formalized analytic tradecraft using something like the Diamond Model for Intrusion Analysis?
Forrester clients, I will also be doing a webinar on this on Monday, December 14, 2015, 11:00 a.m.–12:00 p.m. Eastern time. Register here.
I will leave you with this very important reminder:

The following threat intelligence providers were evaluated in this research: Bitsight Technologies (AnubisNetworks), CrowdStrike, Cyjax, Cytegic, Cyveillance, Digital Shadows, Emerging Threats, FireEye/Mandiant, Flashpoint, IID, Intel 471, iSight Partners, Norse, Recorded Future, SurfWatch Labs, Symantec, Verisign iDefense, Wapack Labs, Webroot, and ZeroFox