Observations on the 2013 Verizon Data Breach Investigations Report
 I was very excited to finally get a copy of the much-anticipated 2013 Verizon Data Breach Investigations Report (DBIR.) I have found the report to be valuable year after year. This is the 6th iteration and this year’s report includes 621 confirmed data breaches, as well as over 47,000 reported security incidents. 18 organizations from across the globe contributed to the report this year. The full report is 63 pages, and I have to say that Wade Baker and company did a great job making it an enjoyable read. I enjoyed the tone, and I found myself laughing several times as I read through it (Laughing and infosec aren't commonly said in the same breath.) There are tons of great references as well, ranging from NASCAR, to Biggie Smalls, the Violent Femmes and more. The mantra of this year’s report is “Understand Your Adversary’ is Critical to Effective Defense and Response.” Here are a few observations:
I was very excited to finally get a copy of the much-anticipated 2013 Verizon Data Breach Investigations Report (DBIR.) I have found the report to be valuable year after year. This is the 6th iteration and this year’s report includes 621 confirmed data breaches, as well as over 47,000 reported security incidents. 18 organizations from across the globe contributed to the report this year. The full report is 63 pages, and I have to say that Wade Baker and company did a great job making it an enjoyable read. I enjoyed the tone, and I found myself laughing several times as I read through it (Laughing and infosec aren't commonly said in the same breath.) There are tons of great references as well, ranging from NASCAR, to Biggie Smalls, the Violent Femmes and more. The mantra of this year’s report is “Understand Your Adversary’ is Critical to Effective Defense and Response.” Here are a few observations:
The focus on the adversary answers customer questions. Who is the adversary? This is a frequent question from Forrester clients. The Mandiant APT1 report stirred up much debate on state sponsored actors and Verizon's data and analysis gives us more perspective on this class of threat actor. The first table in the report profiles the threat actors that are targeting organizations. It provides a high level view that I suggest you include in any type of executive engagement activity you participate in. This 3rd party snapshot of the threat actors should resonate with a wide degree of audiences.
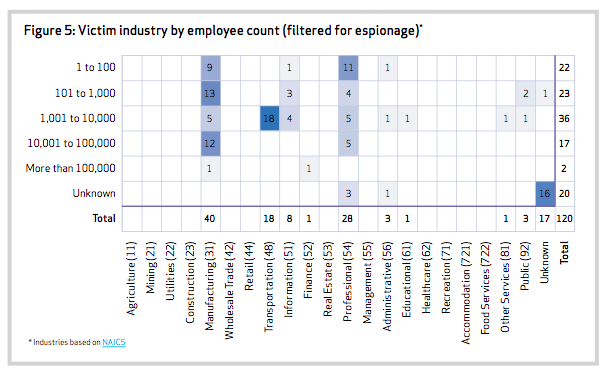
The report also dispels a frequent belief that, “I’m too small to be a target.” Verizon wrote, “We see victims of espionage campaigns ranging from large multi-nationals all the way down to those that have no IT staff at all.” Look at the following figure and you will see many sub 1,000 and sub 100 employee organizations that were the victims of espionage attacks. This same figure can also point out the types of industries espionage attackers target. Manufacturing, transportation, information, professional were the leading industries targeted for espionage. For more information on the industry verticals, check out NAICS.
We have done a TERRIBLE job at stopping phishing. Verizon wrote, "More than 95% of all attacks tied to state- affiliated espionage employed phishing as a means of establishing a foothold in their intended victims’ systems." The traditional email and web content security vendors have responded poorly to the phishing threat vector. This created a huge market opportunity for companies like FireEye to come in and attempt to address a problem that the incumbents were failing at. In response to the competitive threat, we have seen the traditional security players develop and rollout their own features similar to FireEye. These solutions are no silver bullet, and there is little doubt that some victims in the Verizon data set had these “anti-APT” solutions deployed. For more perspective, see my previous blogs: “Avoid The Information Security Squirrel,” “Expense In Depth And The Trouble With The Tribbles,” or “Kim Kardashian And APTs.”
FireEye’s latest threat report also corroborates the use of phishing in espionage. FireEye found phishing to be the primary APT attack vector and saw a 56% increase over Q1 of 2012.
What I’d like to see in the 2014 DBIR. I would like to see Verizon break out of breaches and incidents that resulted from 3rd parties. Using the Verizon threat actor definition, I’d specifically like to see data on external threat actors who compromised companies via 3rd party networks. For example, I want to know how many organizations were attacked via an extranet connection to a supply chain partner. 3rd party risk is a top concern of Forrester clients.
What it means. If you are a potential target for espionage, anti-phishing needs to be one of your core security investments. Before buying any new solutions, I highly suggest that you use professional services from a penetration-testing firm and have them perform targeted testing of your environemnt using phishing scenarios. This could also be peformed by an internal red team. Have the company weaponize malware that exploits both known and unknown vulnerabilities. You need to validate your existing security controls before acquiring new ones. You should use the 3rd party to test products that you are evaluating as well. Use the data from the Mandiant APT1 and the DFIR to help justify the expense of these services. This engagement will probably cost a fraction of any new security controls you might purchase and can help you purchase the most effective protection. You don't want to have to rip and replace a solution because it didn't perform as advertised.
Once you determine that you actually need new technology, there are several anti-phishing approaches that you can take:
1) Network security. Before purchasing a new network-based solution, check with your existing security vendors and find out how they are addressing this threat. Chances are you can leverage a feature that is integrated into your existing portfolio. If the vendor is charging you more for an advanced malware/anti-APT feature, push back and inquire why you are paying for both the failed traditional approach and this new capability. Scalability, global deployments, and SSL inspection can complicate the use of this type of control. Today, almost all network security vendors play in this space.
2) Network visibility. A Network Analysis and Visibility (NAV) solution should be deployed within your environment. When preventive controls fail, and we know they will, we need strong detective controls. These solutions can detect delivery, command and control as well as exfiltration. These types of solutions include: Damballa, Solera Networks, RSA Netwitness, and Lancope Stealthwatch. See: Pull Your Head Out Of The Sand And Put It On A Swivel: Introducing Network Analysis And Visibility
3) Endpoint security. Don’t just rely upon network security based controls that detect delivery of malicious code. You should also use the new breed of endpoint solutions that detect exploitation of malicious code on the host. These types of solutions include: RSA ECAT, SourceFire FireAMP, Trusteer, as well as Bit9. Two other options are Bromium and Invincea which each takes a virtualization based approach to secure the endpoint. Deploying security solutions on endpoints can be challenge for large enterprises with a heterogeneous environment, so you should start small and slowly scale the solution across the organization as it demonstrates operational effectiveness. Start with your high value targets (Executives, administrators.)
Remember to first look to your existing security porfolio and then augment with additional controls as needed. When deploying any security control, you must take a data centric approach and ensure that you have security controls close to the data, not just at the perimeter. Keep in mind that controls will fail and you must have mature incident response capabilities. See Seven Habits Of Highly Effective Incident Response Teams.