Avoid The Information Security Squirrel
"My master made me this collar. He is a good and smart master and he made me this collar so that I may speak. Squirrel!"

In the Pixar film Up, squirrels frequently distract Dug the talking dog. In our space, we are frequently distracted by technology. "I am a good and smart security professional; I must protect my enterprise so that we are secure. APT defense in a box!"
The expo floors at industry events such as the RSA Conference and Blackhat contribute to this. Signage touts the next great piece of technology that will solve all of our security problems. We allow Big Data, security analytics, threat intelligence, and APT defense in a box to distract us. It is easy to do; there is no shortage of challenges for today’s security and risk professional. The threat landscape is overwhelming. We have problems recruiting and retaining the right staff. Day-to-day operational duties take up too much time. Our environments are complex, and we struggle to get the appropriate budget.
These “security technology du jour” solutions are very appetizing. They compel us much like IDS, IPS, and SIM did in the past. We want and need the “easy” button. Sadly, there is no “easy” button and we must understand that threat protection doesn't equal a product or service; there is no single solution. Technology alone isn't the answer we are looking for.

In my latest research, “Seven Habits Of Highly Effective Incident Response Teams,” I discuss how successful Incident Response teams avoid infosec squirrels, and don’t focus exclusively on technology. The foundation of successful Incident Response is effective staff that are augmented with technology and enabled by process and oversight. Possessing the latest technology without staff that is able to properly leverage it is like owning a sports car with an empty tank of gas that you have no clue how to drive. Understanding technology benefits and limitations is one habit of effective Incident Response teams. Here is a preview of the other six steps I discuss in the research:
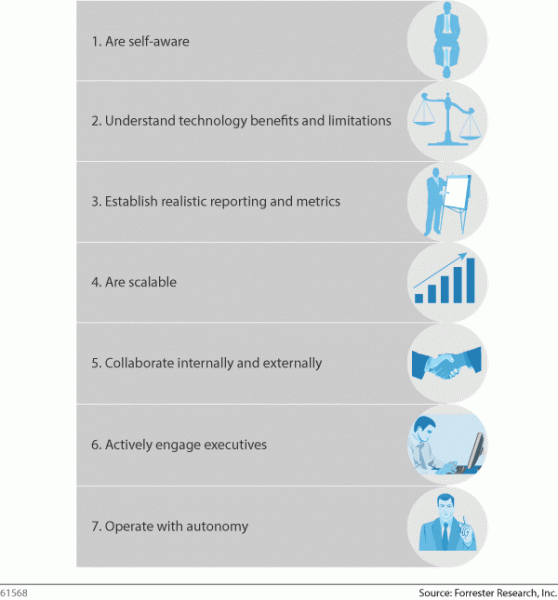
Please let me know what you think and feel free to leave comments.